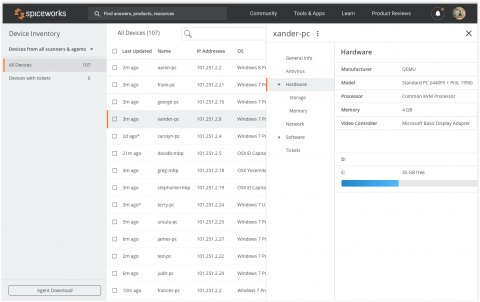
Spiceworks Adds Free Network Inventory Application to its Suite of Integrated Cloud-based Solutions
AUSTIN, Texas — October 9, 2018 — Today at SpiceWorld 2018, Spiceworks announced a new cloud-based Spiceworks Inventory application that integrates with the cloud editions of Spiceworks Help Desk and Spiceworks Remote Support to help IT professionals more intuitively manage their technology assets and support end users from a single, easy-to-use ecosystem.