Operations | Monitoring | ITSM | DevOps | Cloud
Linux
Ubuntu Masters: The masters speak
Canonical and IBM on Technology Enablers for Financial Services
CentOS 8: a clone that reinvents itself
It has taken much longer than usual for the CentOS team to provide us with a new version of their operating system; however, the wait is over. The new CentOS 8 is here. CentOS, or Community ENTerprise Operating System, is a binary-level clone of the RHEL (Red Hat Enterprise Linux) distribution that can be accessed for free. For those unfamiliar with Red Hat, Red Hat offers open source, enterprise-oriented software solutions with enterprise-level support.
A catastrophic flaw in Linux sudo command with a simple fix using Desktop Central
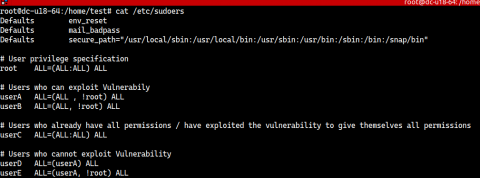
A critical vulnerability in sudo has been disclosed, that when exploited, enables users to bypass security restrictions and execute commands as the root user. This security flaw has to be swiftly remediated as sudo is one of the most integral and commonly used functionalities in Linux operating systems.
How to detect CVE-2019-14287 using Falco
A recent flaw, CVE-2019-14287, has been found in sudo. In this blogpost, we are going to show you how to use Falco or Sysdig Secure, to detect any exploit attempts against this vulnerability. sudo allows users to run commands with other user privileges. It is typically used to allow unprivileged users to execute commands as root. The issue exists in the way sudo has implemented running commands with an arbitrary user ID in versions earlier than 1.8.28.
How to Do Effective Infrastructure Monitoring for Linux with Grafana
Grafana Labs has 8+ clusters in GKE running 270 nodes of various sizes, and all the hosted metrics and hosted log Grafana Cloud offerings are run on 16-core, 64-gig machines. At the recent All Systems Go! conference in Berlin, David Kaltschmidt, Director, User Experience, gave a talk about what monitoring these clusters and servers looks like at Grafana Labs and shared some best practices.
How to Manage Linux Logs
Log files in Linux often contain information that can assist in tracking down the cause of issues hampering system or network performance. If you have multiple servers or levels of IT architecture, the number of logs you generate can soon become overwhelming. In this article, we’ll be looking at some ways to ease the burden of managing your Linux logs.
How to Monitor Syslog Data with Sumo Logic
If you are reading this article, you’re probably familiar with syslog, a logging tool that has been around since the 1980s. It is a daemon present in most Linux-based operating systems. By default, syslog (and variants like rsyslog) on Linux systems can be used to forward logs to central syslog servers or monitoring platforms where further analysis can be conducted. That’s useful, but to make the very most of syslog, you also want to be able to analyze log data.
How to Choose a Linux Distro for Your Server
By Des Nnochiri Whether it’s for network and system administration, database management, web services, or other business functions, chances are you’ll need robust servers as part of your IT infrastructure armory. Traditionally, a server running a Linux operating system has been the preferred option for enterprise use. But which Linux distribution (or distro) is the right one for your particular use case?