Interacting With Log Data in Security Event Manager
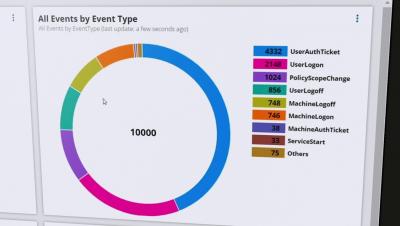
SolarWinds Security Event Manager is designed to give users a centralized view of logs and events occurring across their network, and quickly and easily recall specific logs and identify suspicious patterns and behaviors in that data. This video gives a quick overview of the features in SEM, making it easy for users to view and interact with their log data.