Sysdig Secure 2.4 introduces runtime profiling for anomaly detection + new policy editor for enhanced security.
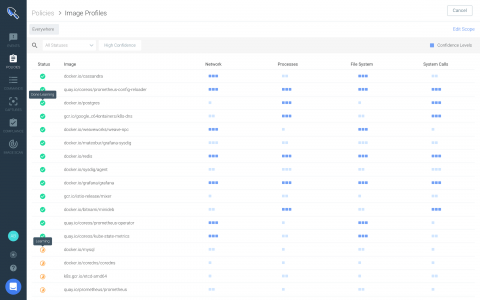
Today, we are excited to announce the launch of Sysdig Secure 2.4! With this release, Sysdig adds runtime profiling to enhance anomaly detection and introduces brand new interfaces that improve runtime security policy creation and vulnerability reporting. These features are focused on upgrading the experience of creating your security policy to detect security threats and attacks to your infrastructure and apps.