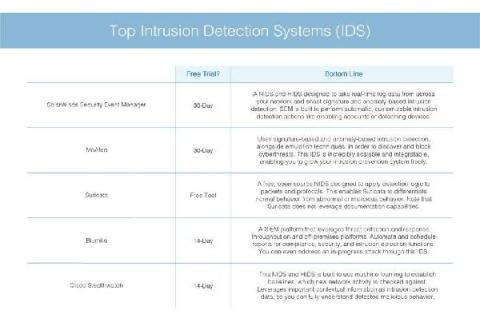
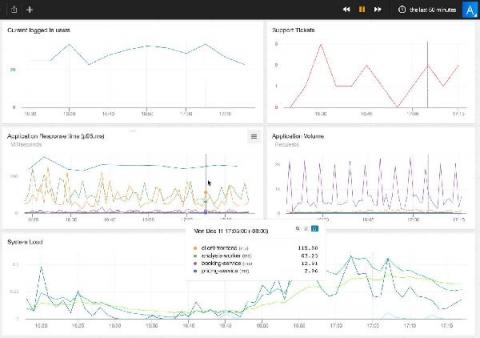
Featured Post
How You Can Make Your Database More Efficient
Data is the lifeblood of your business, critical to its survival and success. It delivers insights into customers' specific needs, helping you better understand them and deliver a more tailored user experience. With data playing such a key role in whether modern businesses sink or swim, it's vitally important to optimize your database to ensure data is insightful, relevant, and actionable, providing the end user with the best possible experience.