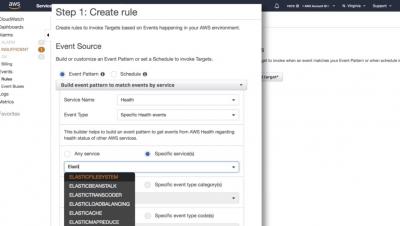
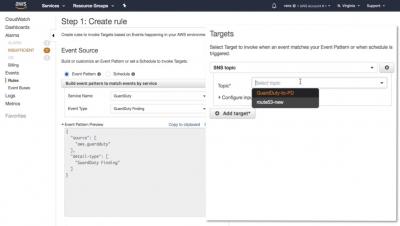
After Agile, DevOps, and Lean IT: Modern Methodology in the Age of Disruption
In an age of disruption, increasingly complex and chaotic problems demand emergent or completely novel practices. Decades-old practices no longer work, raising difficult questions about the role of management in a world being disrupted by technology.