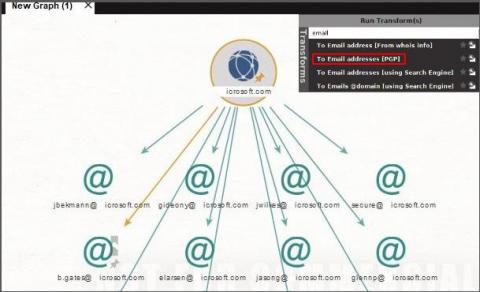
Ubuntu 20.04 LTS to enforce stronger TLS v1.2 encryption by default
In Ubuntu 20.04 LTS, the OpenSSL 1.1.1f library has been modified to use Security Level 2 by default (previous versions of Ubuntu use Security Level 1). Security Level 2 guarantees that protocols, key exchange mechanisms, cipher suites, signature algorithms, certificates and key sizes provide a minimum of 112 bits of message secrecy. In practice, it means that RSA keys are required to be at least 2048 bits long and ECC keys at least 224 bits using the SHA256 certificate signature algorithm.