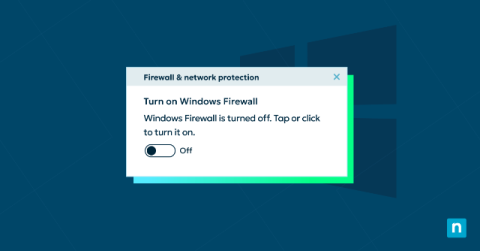
Managing Your Windows Firewall Notifications in Windows 10
Windows Firewall notifications is a crucial component of Windows 10’s security infrastructure. They are an extension of this protection, informing users about critical security events, such as attempts to access the network or changes to security settings. Understanding how and when to enable or disable these notifications can help IT professionals and Windows users optimize their security settings while minimizing distractions.