Operations | Monitoring | ITSM | DevOps | Cloud
Data Breaches
The Rising Tide of Data Breach Awareness
There’s an old saying that “there’s no such thing as bad publicity.” Unfortunately, this doesn’t ring true when it comes to data breaches and ransomware attacks. High profile security incidents continue to make headlines, and those headlines are impacting bottom lines. In response to these, the US federal government is modernizing its own cybersecurity infrastructure, and more state governments are implementing laws to protect citizens.
Cybersecurity with Ubuntu
The cybersecurity state of affairs can be described as too complex today. There is an enormous number of threats endangering sensitive data for the average IT team to cope with. Threats ranging from exposure of physical assets stored in an office, to “social engineering” attacks resulting in unauthorized access, or even threats that exploit obscure software vulnerabilities.
Kubernetes security issues: An examination of major attacks
In a never-ending game of cat and mouse, threat actors are exploiting, controlling and maintaining persistent access in compromised cloud infrastructure. While cloud practitioners are armed with best-in-class knowledge, support, and security practices, it is statistically impossible to have a common security posture for all cloud instances worldwide. Attackers know this, and use it to their advantage. By applying evolved tactics, techniques and procedures (TTPs), attackers are exploiting edge cases.
Red Canary says 43% Lack Readiness to Notify Customers of a Security Breach
Thoughts On the Codecov Breach
It was revealed just a few days ago that US Federal investigators are looking into an intrusion and insertion of malicious code into Codecov. As many readers here will already know, Codecov is a software auditing tool that analyses your source code to check for the amount of test coverage. The intrusion targeted the Codecov bash uploader, which is a script that provides a way to send coverage reports to Codecov.
The Facebook data breach that affects over 533 million users explained
If you’re a Facebook user, brace yourself for this one. It’s recently come to light that 533 million Facebook users’ details were found on a very suspicious hacker forum. The details found include users’ phone numbers, Facebook IDs, full names, locations, birthdays, and email addresses – all typical information that is stored on a Facebook account.
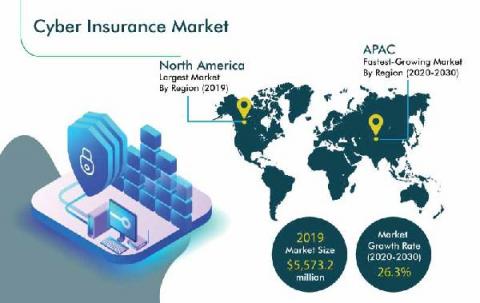
The Complete Guide to Data Breach Insurance
It’s been noted that there are two types of organizations – those that have suffered a data breach, and those that will fall victim to a data breach sooner than later (most likely sooner). The hard truth of this statement is reflected in the fact that according to some sources 97% of networks will experience a security compromise over any given six-month period. And with a staggering 9.7 billion data records having been breached since 2013, these numbers are only rising.
5 Common Elasticsearch Mistakes That Lead to Data Breaches
Avon and Family Tree aren’t companies you would normally associate with cybersecurity, but this year, all three were on the wrong side of it when they suffered massive data breaches. At Avon 19 million records were leaked, and Family Tree had 25GB of data compromised. What do they have in common? All of them were using Elasticsearch databases. These are just the latest in a string of high profile breaches that have made Elasticsearch notorious in cybersecurity.
7 High-Risk Events to Monitor Under GDPR: Lessons Learned from the ICO's BA Penalty Notice
Hello Security Ninjas, Today's IT world is complex and can be challenging for security operations teams. Nowadays, more apps are being integrated and interconnected than ever before. Cloud services and SaaS solutions purchased all throughout the organization outside of the IT department add even more complexity. Communicating to application and service owners the kind of activities that need to be logged and sent to the SOC can be a daunting task.