Operations | Monitoring | ITSM | DevOps | Cloud
ManageEngine
Setting up a service catalog for your remote workforce with ServiceDesk Plus
Solve storage monitoring woes with OpManager
Data in your enterprise organization doubles almost every year, and data multiplication at this pace requires boosting your storage capacity. But when the magnitude of data size increases, latency or performance lags are inevitable. You can outsource your storage infrastructure management to a third-party, but this might place your data at risk from security threats. The correct approach is to install a dedicated storage monitoring solution in your network. Fair enough! But is it essential?
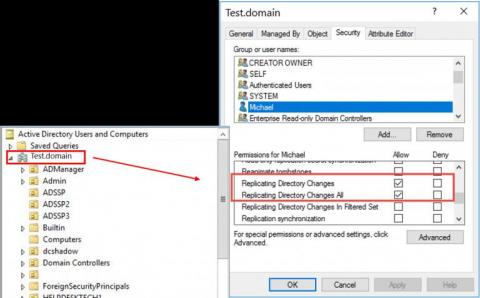
IT security under attack blog series: Instant domain persistence by registering a rogue domain controller
In this blog in the IT security under attack series, we will learn about an advanced Active Directory (AD) domain controller (DC) attack to obtain persistence in AD environments. Dubbed DCShadow, this is a late-stage kill chain attack that allows a threat actor with admin (domain or enterprise admin) credentials to leverage the replication mechanism in AD to register a rogue domain controller in order to inject backdoor changes to an AD domain.
The Building Company: "Building" the future with OpManager
The Building Company serves the full spectrum of the construction industry including the residential, commercial, and industrial markets. The retail activities of the company are provided through 124 outlets throughout Southern Africa. Operations are located in major centers in South Africa, Namibia, Botswana, and Swaziland, and are managed as either corporate, joint venture, or franchise stores.
6 ways to use analytics to deliver an exceptional end-user experience: Part 2
Welcome to the second part of our three-part blog series on leveraging analytics to deliver an exceptional end-user experience. In the last part, we discussed two key points: how to gauge the effectiveness of your support forms using analytics, and how to pick the right metrics that focus on customer satisfaction. In this part, we’ll discuss the next two ways analytics can help you deliver an exceptional end-user experience.
Five worthy reads: The rise in credential stuffing attacks
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week we explore how credential stuffing attacks are evolving and why they pose a greater threat than meets the eye. Credential stuffing is perhaps the simplest form of cyberattack, but it continues to make headlines despite its lack of sophistication. It has become the attack method of choice for cybercriminals primarily because of its high success rate and ROI.
5 user behavioral patterns to look out for in a decentralized workspace
Problem: If there are thousands of employees scattered around hundreds of places, how do you keep your organization’s network safe? Solution: You should monitor your employees wherever they’re located, and devise a standard baseline of their behavior through machine learning techniques. By using that information, you can identify anomalies and protect your network from cyberattacks.
Why every IT admin needs a hardware monitor, and what it can do for your organization's business continuity
The ITIC 2020 Global Server Hardware, Server OS Reliability Report released in April found that reliability declined in 67 percent of servers over four years old when corporations failed to retrofit or upgrade the hardware to accommodate increased workloads. This highlights the pressing need for hardware monitor solutions and the need for immediate alerting mechanisms to ensure the longest possible lifespan for hardware.