The what, why, and how of using network IP scanners in IP-centric IT infrastructures
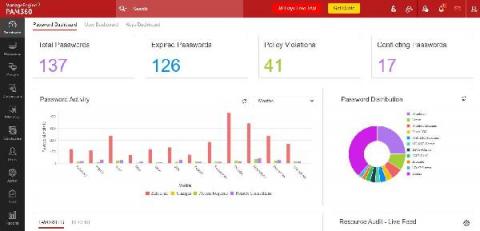
A simple command-line interface (CLI) ping will give you details about your target IP address. However, you may have to input the ipconfig command, and then the arp-a command to fully discover the status of an IP, and this is just for one IP address. Now imagine doing this for an IP block of 300 IPs, or even 50 IPs, or doing the same task periodically to manage your IP pool of thousands of addresses and their metrics. Seems like an Herculean task for any network admin!