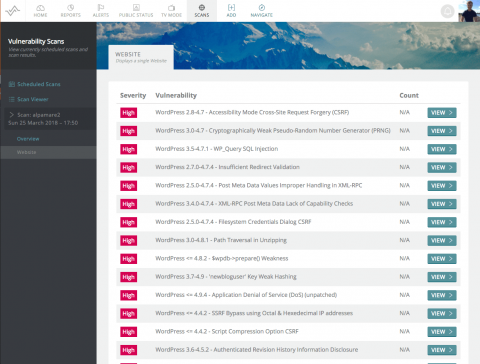
WordPress Security Scanning
With WordPress powering over 30% of the internet and a plugin ecosystem that allows anyone to write software which will execute code on your server, it’s no wonder that it’s become a popular target for hackers. As part of our Vulnerability Scanning service – which already checks for thousands of known software and configuration vulnerabilities for all major software products and operating systems – we now also test over 10,000 known WordPress vulnerabilities.