Operations | Monitoring | ITSM | DevOps | Cloud
Data Security
Data Protection Plan: Guide & 8 Steps for Creation
There has been a sharp increase in the amount of personal and organizational data that is stored online and on devices. Losing this data could result in disastrous consequences for businesses or individuals, which means that data protection is certainly necessary. Data protection plans are essential for the safety and security of data within all organizations.
Redgate Software Adopts Policy-Driven Approach to Data Protection with New Data Catalog Release
5 Ways To Prevent Unauthorized Access to Your Company Data
N-able Introduces Cove Data Protection
How Privacy Organizations and NGOs Help Build a Better Society
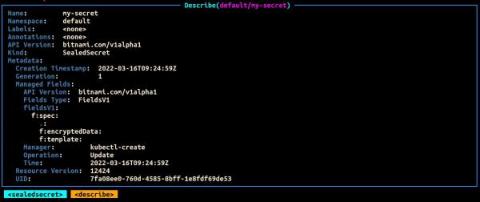
Managing Sensitive Data in Kubernetes with Sealed Secrets and External Secrets Operator (ESO)
Having multiple environments that can be dynamically configured has become akin to modern software development. This is especially true in an enterprise context where the software release cycles typically consist of separate compute environments like dev, stage and production. These environments are usually distinguished by data that drives the specific behavior of the application.
What is Data Encryption and Why It's Recommended for Really Safe Online Security
How FinTechs can ramp up data security in 2022
Better Protect your Corporate Data While Ensuring Optimal Service Delivery for your Business Lines
Within an organization, the Network Operations Center (NOC) and Security Operations Center (SOC) teams need to work together to maintain optimal network performance in addition to ensuring both overall security and the availability of IT services for business lines. In the past, these two teams were focused on two separate objectives, using different tools to do so and often running specific processes.