Operations | Monitoring | ITSM | DevOps | Cloud
PCI
New Features to Meet Upcoming Ecommerce Security Regulations
Understanding How OpenTelemetry can help with PCI Compliance
RapidSpike PCI & GDPR Audit
Using RapidSpike to Support PCI DSS 4.0 Compliance
The latest version of the PCI DSS (Payment Card Industry Data Security Standard) is version 4. We are currently in the transition period following the publication of the new standard, heading towards full implementation.
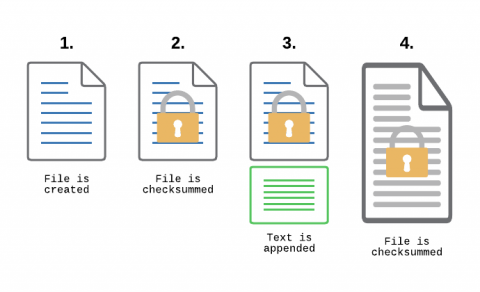
Monitoring Transaction Log Files for PCI compliance
File Integrity Monitoring, aka as FIM, is a must-have feature for anyone in charge of security. With FIM, one can detect when a critical file, such as a file that belongs to the Operating System, or a key configuration file, is changed. In most cases, configuring FIM is straightforward: If the file changes then generate an alert.
PCI DSS - Requirements and Levels of Compliance
The security of payments is underlined in multiple visuals we confront each day while visiting numerous websites and apps. Can businesses and customers benefit from that? Any company handling cardholder data, whether a startup or an enterprise, must adhere to the Payment Card Industry Data Security Standard (PCI DSS). You must validate your compliance annually in order to remain compliant.
PCI DSS 4.0: Protecting Payment Card Processing
PCI? PCI SSC? PCI DSS 4.0? Need these acronyms explained? Well, this blog is for you. Read on to find out how the new PCI DSS 4.0 (a set of security standards created to ensure companies maintain a secure financial environment) will affect how you transact online, monitor your website payment gateways and more.
Achieving PCI DSS Compliance in the Cloud
In the current digital world, businesses should ensure that they protect cardholders’ data at all costs. As such, any business that stores, processes, or transmits cardholder data or any other sensitive information should comply with the latest Payment Card Industry Data Security Standards released in 2018. However, this can be overwhelming for most decision-makers. Below is a guide on how you can achieve PCI DSS compliance for your cloud operations.
Cloud-Centric PCI Compliance Demands Cloud-Native Controls
Over the last 15-plus years, the Payment Card Industry Data Security Standard – a.k.a. PCI DSS – has endured as the bellwether of IT security standards. For today’s e-commerce vendors and cloud centric retailers, maintaining alignment with “PCI” remains as relevant as ever, especially given the continued proliferation of threats and diversity of cloud and hybrid environments.