Defense in depth: DoublePulsar
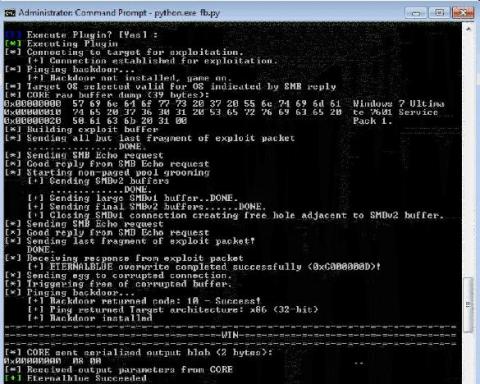
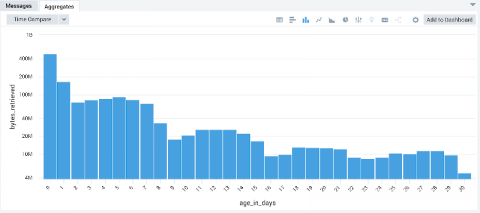
Unless you’ve been living under a rock you are probably familiar with the recent Shadow Brokers data dump of the Equation Group tools. In that release a precision SMB backdoor was included called Double Pulsar. This backdoor is implemented by exploiting the recently patched Windows vulnerability: CVE-2017-0143. For detection, we are going to first focus on the backdoor portion of the implant, hunting for traces left behind on the network.