Work from home better with secure and reliable enterprise service
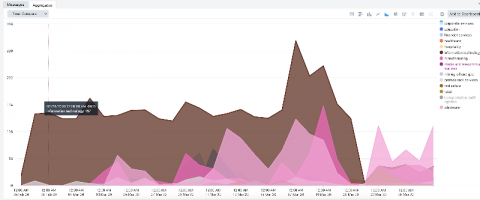
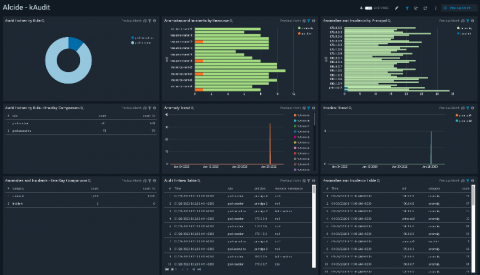
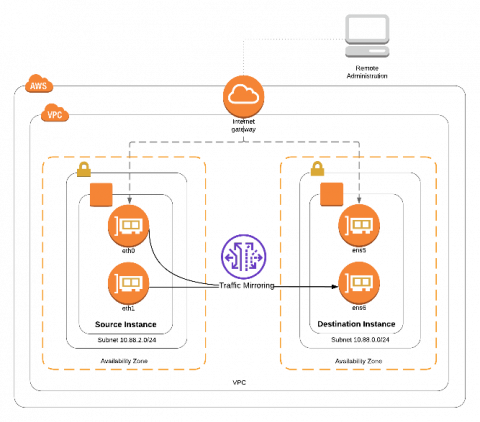
Today, we are facing an unprecedented situation. The COVID-19 pandemic is affecting everything we know -- our families, our businesses, our communities, and our way of life. In these tough times, many organizations have resorted to mandatory remote working for employees so they can still be productive and safe. Saas productivity tools like Zoom, Slack, G-Suite and Office 365 became seemingly mandatory in this new distributed workplace.