Spam In the Browser
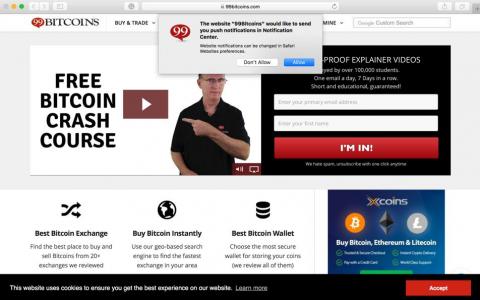
A new kind of spam is being observed in the field that uses the browser notification feature to trick users into subscribing to sites that will in turn bombard users with notifications usually related to click or add profit schemes. Subscription notification request seen below: Browser notification subscription requests are a legitimate feature that allows visitors of a site to be notified when there is new content available. It saves users the need to constantly refresh or keep open browser tabs.