Continuous Intelligence for Atlassian tools and the DevSecOps Lifecycle (Part 1)
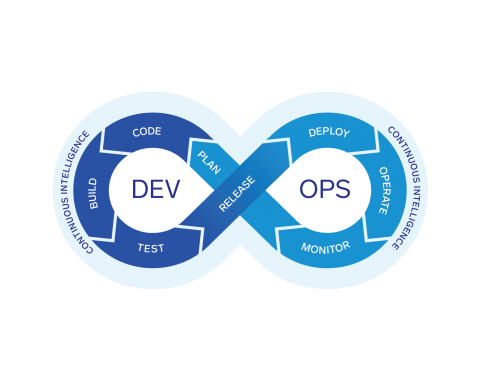
Implementing and operationalizing the best practices and capabilities of DevOps into an organization is a key predictor for increased customer satisfaction, organizational productivity and profitability. Doing so successfully can be a challenging endeavour. Implementing DevOps can be particularly difficult because it oftentimes requires technology changes, process changes and a drastic change in mindset.