Building better software faster - the key to successful digital transformation
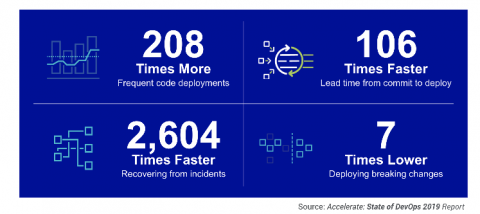
As digital transformation accelerates across all industries, it has become increasingly important for businesses to get better, much better at the development and delivery of new software to drive revenue and engage customers in new ways. Ironically, most businesses are flying blind in how they track, benchmark and optimize their software development. Teams that consistently innovate and deliver new, high quality software quickly generate significant competitive advantage for their companies.