Operations | Monitoring | ITSM | DevOps | Cloud
Containers
The latest News and Information on Containers, Kubernetes, Docker and related technologies.
Collecting Kubernetes Data Using OpenTelemetry
Running a Kubernetes cluster isn’t easy. With all the benefits come complexities and unknowns. In order to truly understand your Kubernetes cluster and all the resources running inside, you need access to the treasure trove of telemetry that Kubernetes provides. With the right tools, you can get access to all the events, logs, and metrics of all the nodes, pods, containers, etc. running in your cluster. So which tool should you choose?
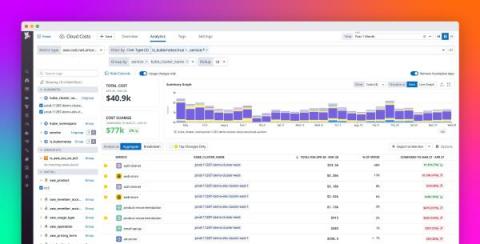
Understand your Kubernetes and ECS spend with Datadog Cloud Cost Management
Rising container usage has fueled a growing reliance on container orchestration systems such as Kubernetes, EKS, and ECS. As organizations increasingly opt to run these systems in the cloud, their cloud spend tends not only to grow but also to become more opaque due to the dynamic complexity of these environments. Typically, various services, teams, and products share cluster resources, and as nodes are added and removed, those resources continuously shift.
What Is an Application Programming Interface (API)? - VMware Tanzu Fundamentals
Merging to Main #3: CI/CD Secrets
The Future of DevOps and Platform Engineering - Civo.com
Visualizing service connectivity, dependencies, and traffic flows in Kubernetes clusters
Today, the cloud platform engineers are facing new challenges when running cloud native applications. Those applications are designed, deployed, maintained and monitored unlike traditional monolithic applications they are used to working with. Cloud native applications are designed and built to exploit the scale, elasticity, resiliency, and flexibility the cloud provides. They are a group of micro-services that are run in containers within a Kubernetes cluster and they all talk to each other.
8 Business Benefits of Ephemeral Environments
Ask What Air-Gapping Can Do for You
In our recent webinar on air-gapped security, D2iQ VP of Product Dan Ciruli shared a new way of thinking about air-gapping, explaining how air-gapping could be applied in places that are not usually considered candidates for air-gapping. In an exchange of insights with Paul Nashawaty, principal analyst at Enterprise Strategy Group, Ciruli explained how the need for air-gapped security has become more critical as more organizations move to the cloud.
Understanding Kubernetes Logs and Using Them to Improve Cluster Resilience
In the complex world of Kubernetes, logs serve as the backbone of effective monitoring, debugging, and issue diagnosis. They provide indispensable insights into the behavior and performance of individual components within a Kubernetes cluster, such as containers, nodes, and services.