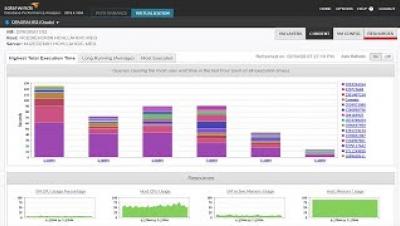
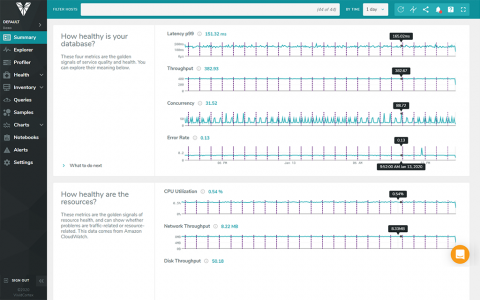
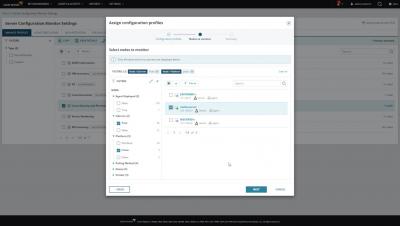
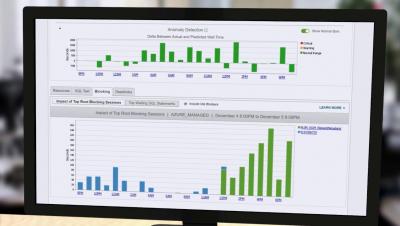
Papertrail + Python Logging = Super Powers
Design applications to be modular. It’s a software design best practice. Modular programming is writing multiple independent programs that perform a single function but work together to achieve an overarching outcome. The benefit to this design is the smaller parts can be easily created and tested. New functionality can be slipped into the larger whole without interfering with other functions.