Operations | Monitoring | ITSM | DevOps | Cloud
Threat Hunting
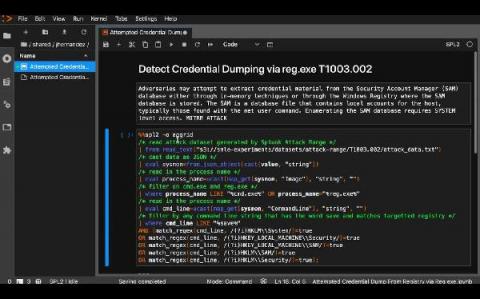
Threat Hunting with Threat Intelligence
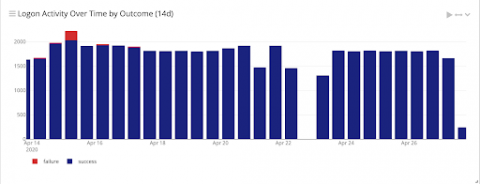
With more people working from home, the threat landscape continues to change. Things change daily, and cybersecurity staff needs to change with them to protect information. Threat hunting techniques for an evolving landscape need to tie risk together with log data. Within your environment, there are a few things that you can do to prepare for effective threat hunting. Although none of these is a silver bullet, they can get you better prepared to investigate an alert.
Threat Hunting With ML: Another Reason to SMLE
Security is an essential part of any modern IT foundation, whether in smaller shops or at enterprise-scale. It used to be sufficient to implement rules-based software to defend against malicious actors, but those malicious actors are not standing still. Just as every aspect of IT has become more sophisticated, attackers have continued to innovate as well. Building more and more rules-based software to detect security events means you are always one step behind in an unsustainable fight.
How Clorox leverages Cloud SIEM across security operations, threat hunting, and IT Ops
Investigative analysis of disjointed data in Elasticsearch with the Siren Platform
At Siren, we build a platform used for “investigative intelligence” in Law Enforcement, Intelligence, and Financial Fraud. Investigative intelligence is a specialisation of data analytics that serves the needs of those that are typically hunting for bad actors. Such investigations are the primary focus of law enforcement and intelligence, but are also critical to uncovering financial crime activities and for threat hunting in cybersecurity.
Gaining holistic visibility with Elastic Security
Let’s talk visibility for a moment. Security visibility is a data-at-scale problem. Searching, analyzing, and processing across all your relevant data at speed is critical to the success of your team’s ability to stop threats at scale. Elastic Security can help you drive holistic visibility for your security team, and operationalize that visibility to solve SIEM use cases, strengthen your threat hunting practice with machine learning and automated detection, and more.
Threat hunting capture the flag with Elastic Security: BSides 2020
Last month, members of the Elastic Security team hosted a threat hunting capture the flag (CTF) event at BSides SATX. We provided the community with an environment to learn and practice threat hunting with our team, and cultivated new relationships with attendees. By sharing information with security practitioners, we can help prepare them to defend their organization’s data from attack through knowledge transfer.