Operations | Monitoring | ITSM | DevOps | Cloud
SIEM
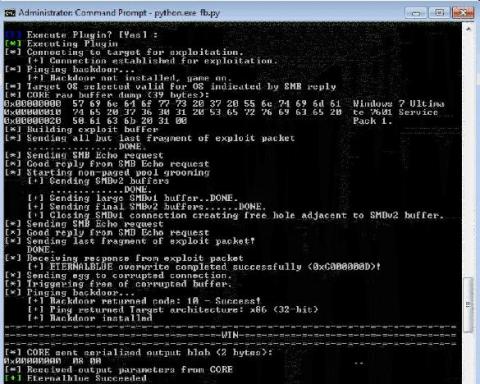
Integrating Attack Behavior Intelligence into Logstash Plugins
Preventing "copy-paste compromises" (ACSC 2020-008) with Elastic Security
The Australian Cyber Security Centre (ACSC) recently published an advisory outlining tactics, techniques and procedures (TTPs) used against multiple Australian businesses in a recent campaign by a state-based actor. The campaign — dubbed ‘copy-paste compromises’ because of its heavy use of open source proof of concept exploits — was first reported on the 18th of June 2020, receiving national attention in Australia.
What is SIEM?
SIEM (Security Information and Event Management) is a kind of software whose purpose is to provide organizations and corporations with useful information. “About what?” you may wonder. Well, about potential security threats related to your business networks. SIEM does this through data collation and by prioritizing all kinds of dangers or threats. In general, we already answered the question “what is SIEM?”, but how does it do it?
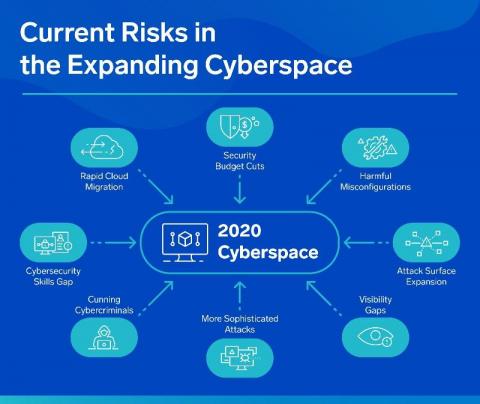
Why cloud-native SIEM is vital to closing the security skills gap
Journey of Elastic SIEM Getting Started to Investigating Threats: Part 2
How to Overcome the Drawbacks of SIEM Tools
These days, “SIEM” (Security Information and Event Management) is all over the place. SIEM tools work by collecting data from multiple systems and noticing patterns in the data. This adds immediate value to the business by providing insights, security recommendations, and actionable intelligence. Despite being helpful tools for many companies, SIEM tools do have their drawbacks. This article will describe the four main ones and offer suggestions for how they might be overcome.
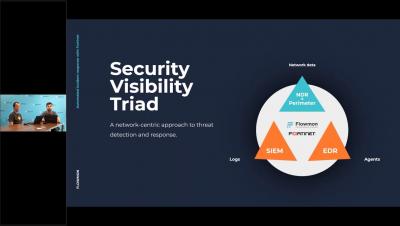
Automated incident response with Flowmon and FortiGate
Getting started with adding a new security data source in your Elastic SIEM: Part 1
What I love about our free and open Elastic SIEM is how easy it is to add new data sources. I’ve learned how to do this firsthand, and thought it’d be helpful to share my experience getting started. Last October, I joined Elastic Security when Elastic and Endgame combined forces. Working with our awesome security community, I’ve had the opportunity to add new data sources for our users to complement our growing catalog of integrations.