Unify APM and RUM data for full-stack visibility
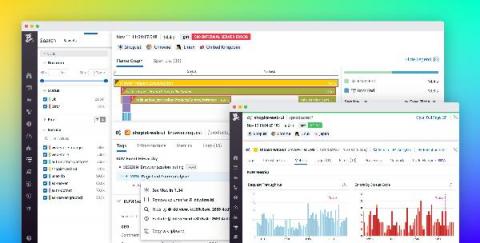
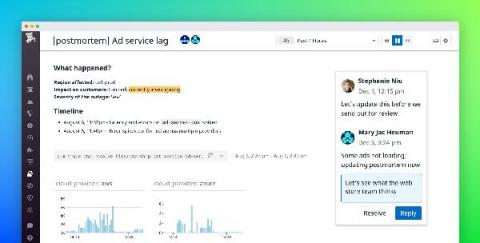
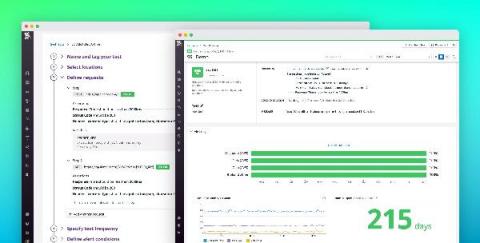
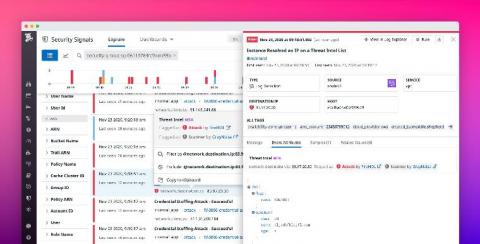
Without unified visibility across your entire stack, it can be difficult to investigate backend dependencies when troubleshooting frontend issues, or to track the source of database failures that originate from bad browser requests. Full-stack visibility gives you the insight you need to pinpoint and resolve incidents quickly.