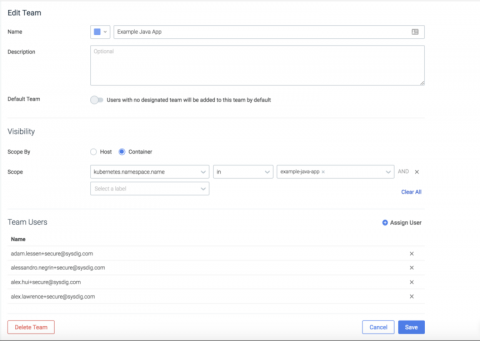
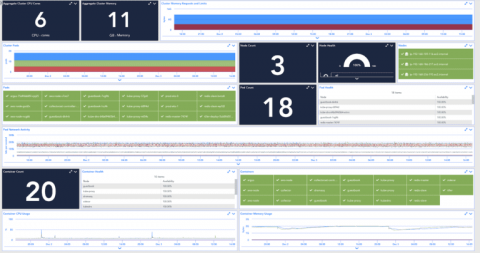
How to Get Started with Rancher's New Multi-Tenant Prometheus Support and Alpha Release Process
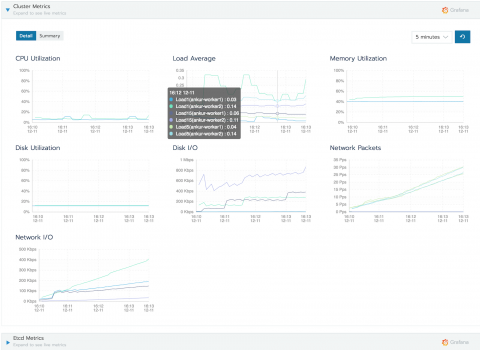
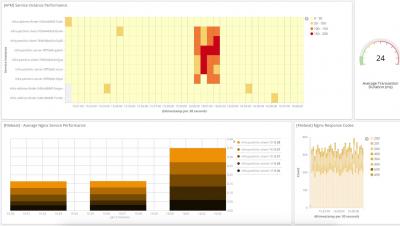
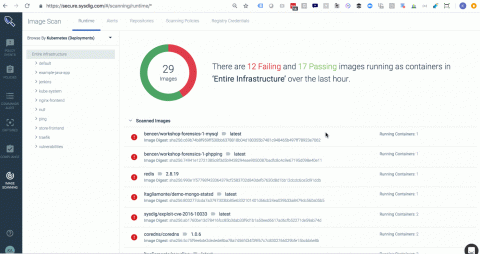
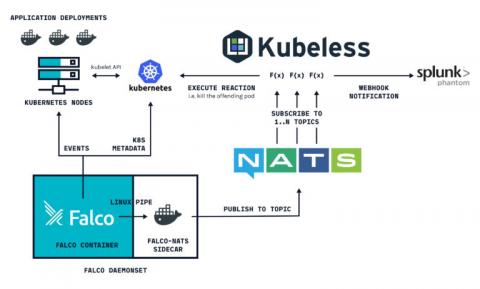
Ankur Agarwal, Rancher's Head of Product Management, describes new features in Rancher 2.2. Learn how to monitor multiple Kubernetes clusters in this step-by-step tutorial and how our Alpha Release process works.