Operations | Monitoring | ITSM | DevOps | Cloud
CI CD
The latest News and Information on Continuous Integration and Development, and related technologies.
How to Secure Your CI/CD Pipeline: Best Tips and Practices
CI/CD pipelines have become a cornerstone of agile development, streamlining the software development life cycle. They allow for frequent code integration, fast testing and deployment. Having these processes automated help development teams reduce manual errors, ensure faster time-to-market, and deliver enhancements to end-users. However, they also pose risks that could compromise stability of their development ecosystem.
Trivial? THIS is What Developers Really Mean!
Do you think of software developer toil like Atlassian, LaunchDarkly, Okteto and Sleuth?
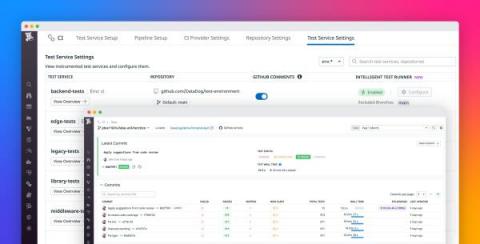
Streamline your CI testing with Datadog Intelligent Test Runner
Modern continuous integration (CI) practices enable development teams to quickly and efficiently build and deploy application code to a shared codebase. However, deploying new code is typically accompanied by tests, and as the codebase expands, this results in a proportionately larger test suite.
Platform Team Demo
Zero trust security for CI/CD pipelines
The zero trust security model is an approach to network security that enforces strict access controls and authentication at every stage of the software development lifecycle. It treats every user, device, and transaction as a security risk and uses the principle of least privilege to restrict access to sensitive resources and minimize the potential attack surface.
Got tool sprawl? Let's consolidate.
A guide to static application security testing (SAST)
Static application security testing (SAST) involves analyzing source code to identify and address potential security vulnerabilities. Using SAST early in development identifies threats before they can affect a live environment. SAST is particularly important for continuous integration and continuous deployment (CI/CD) pipelines. These pipelines automate the integration of new code changes into the main codebase and deploy applications to production environments.
Continuous Delivery Pipeline for Kubernetes Using Spinnaker
Kubernetes is now the de-facto standard for container orchestration. With more and more organizations adopting Kubernetes, it is essential that we get our fundamental ops-infra in place before any migration. In this post, we will learn about leveraging Jenkins and Spinnaker to roll out new versions of your application across different Kubernetes clusters.