Operations | Monitoring | ITSM | DevOps | Cloud
Threat Detection
Five worthy reads: Threat intelligence-the key to proactive cybersecurity
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we explore how cyber threat intelligence can aid organizations. Enterprises often end up spending a great deal of money on monitoring and wiring their perimeter with defensive security solutions. But is merely incorporating security solutions like firewalls, antivirus software, intrusion detection systems, web filtering, and encryption enough?
Signal Sciences brings real-time web attack visibility to Datadog
Signal Sciences is proud to announce our integration with the Datadog platform. This integration furthers our mission of producing the leading application security offering that empowers operations and development teams to proactively see and respond to web attacks—wherever and however they deploy their apps, APIs, and microservices.
Integrating Threat Intelligence into Graylog 3+
In this post, I will describe in detail how to use the Threat Intelligence plugin that ships with Graylog. I’ll start with the steps necessary to prepare your data, then explain how to activate the feature and how to configure it for use.
The what, why, and how of unified endpoint management
IT management has become a department that exists in every business ecosystem, irrespective of verticals. Those who are responsible for taking care of IT management need to work around the clock to secure and maintain servers, computers, smartphones, tablets, iPads, IoT devices, virtual machines, and more. The technician alone is like a modern puppeteer controlling and manipulating all these devices from one, central location in a unified way.
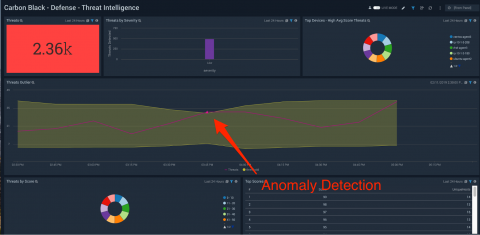
Endpoint Security Analytics with Sumo Logic and Carbon Black
As the threat landscape continues to expand, having end-to-end visibility across your modern application stack and cloud infrastructures is crucial. Customers cannot afford to have blind spots in their environment and that includes data being ingested from third-party tools.
Network Security Monitoring with Suricata, Logz.io and the ELK Stack
Suricata is an open source threat detection system. Initially released by the Open Information Security Foundation (OISF) in 2010, Suricata can act both as an intrusion detection system (IDS), and intrusion prevention system (IPS), or be used for network security monitoring.
Five worthy reads: AI and ML: Keys to the next layer of endpoint protection
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we’ll talk about why incorporating AI into your UEM strategy may be inevitable.
Conquer it with correlation-Part 1: The advanced persistent threat (APT)
Among all the pesky attacks that keep security administrators working late, advanced persistent threats (APTs) are possibly the most lethal. An APT is a long-term, targeted attack which involves stealthily spying on an organization’s network activity or siphoning off sensitive data, as opposed to openly damaging or locking down network resources.