Detect CVE-2020-8554 using Falco
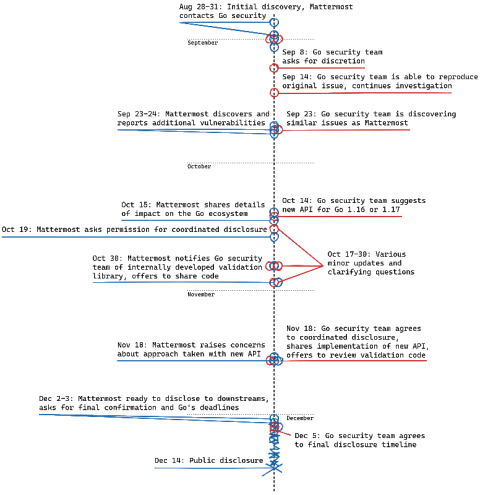
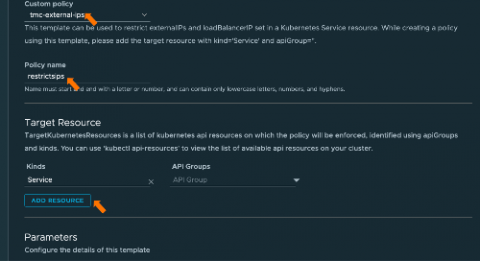
CVE-2020-8554 is a vulnerability that particularly affects multi-tenant Kubernetes clusters. If a potential attacker can create or edit services and pods, then they may be able to intercept traffic from other pods or nodes in the cluster. An attacker that is able to create a ClusterIP service and set the spec.externalIPs field can intercept traffic to that IP. In addition, an attacker that can patch the status of a LoadBalancer service can set the status.loadBalancer.ingress.ip to similar effect.