The New Sumo Logic AWS Security Quick Start
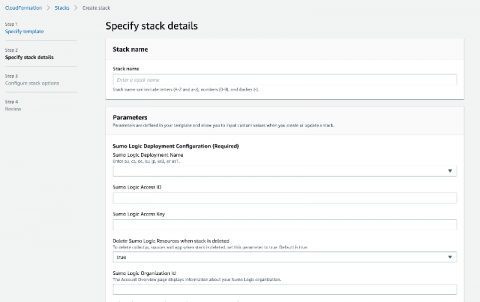
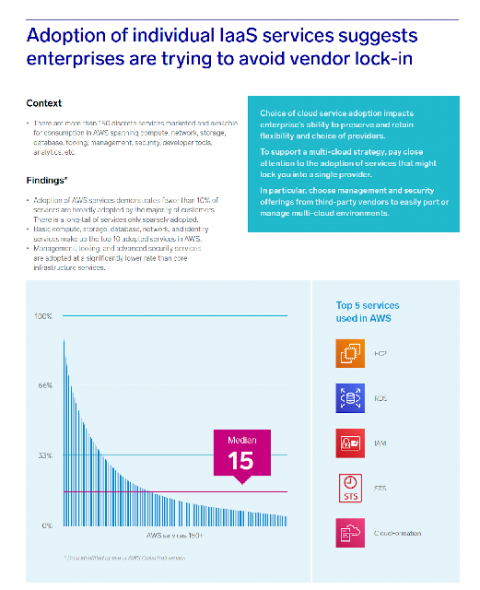
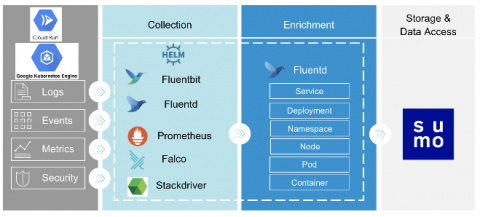
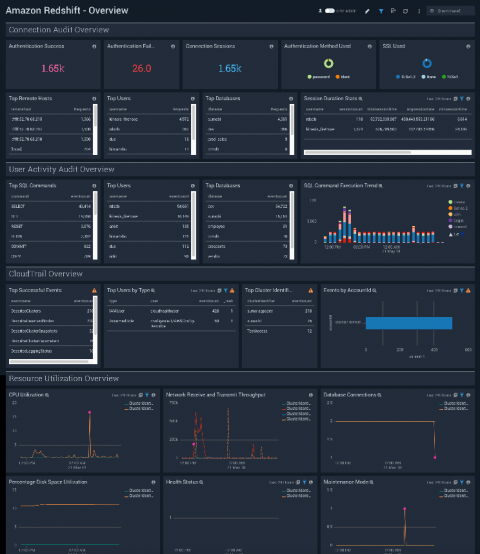
Security is a top concern for any enterprise to move their applications and workloads to the public cloud. AWS offers a broad selection of native security tools and as our Continuous Intelligence Report noted, AWS customers are using several of these to improve the security of their AWS environment. However, it can be overwhelming to know where to start and how to deploy best practices for detecting security misconfigurations caused by human errors and attacks from external sources.