Cloud SIEM: Getting More Out of Your Threat Intelligence - 3 Use Cases for IOCs
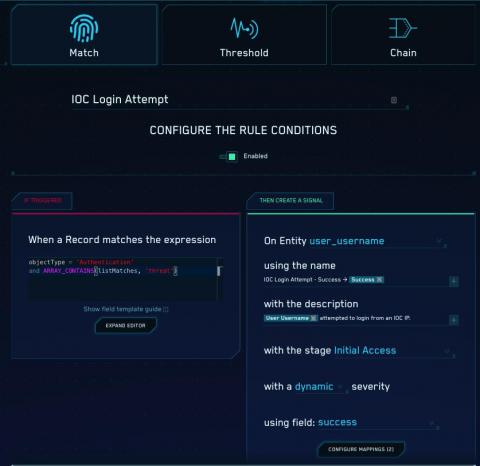
Ever since JASK was founded, we have heavily integrated with threat intelligence platforms to gain context into attacker activity through indicators of compromise (IOCs). Now that we have joined Sumo Logic, our customers have the ability to pull in more data than ever making this feature even more powerful. One of our tightest integrations is with the Anomali (formerly ThreatStream) platform.