Micro Lesson: Using Your Data in Sumo Logic
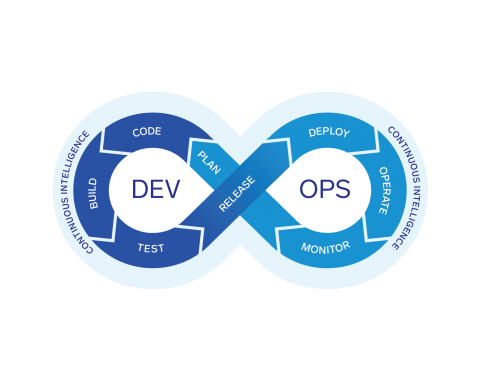
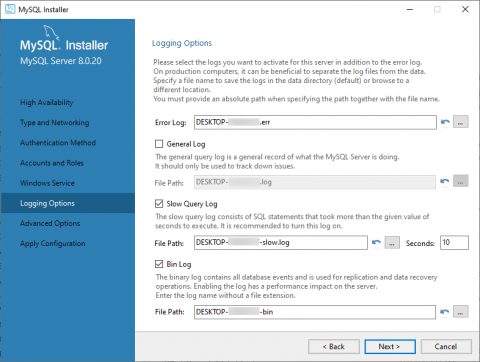
This video gives a brief outline of your Sumo journey that includes getting your data into Sumo Logic, analyzing, visualising, and monitoring your data, and sharing your findings that are eventually helpful in taking the key decisions.