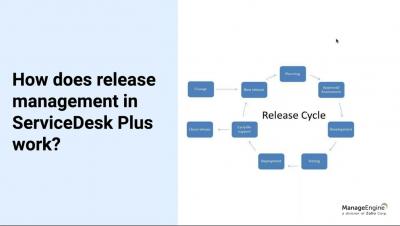
Introduction to Hardware Asset Management
IT asset management is a critical part of any IT infrastructure management team. When done correctly, IT asset management can bring significant cost savings to your organization, and ensure that the IT support you're providing is quick and efficient.