Optimize Value of Cloudtrail Logs With Infrequent Tier
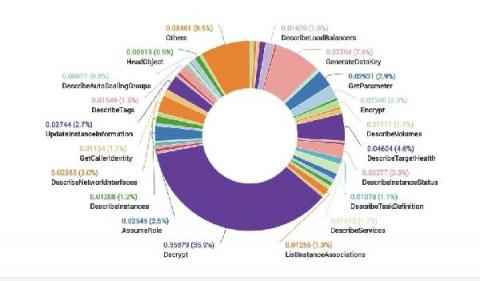
A common scenario for log analytics is that many log events are high value for real time analytics, but there are also events that are low value for analytics, but account for a very large percentage of overall log volume. Often these same low value logs are used only for ad-hoc investigations from time to time or need to be retained for audit purposes.