IT security under attack: Credential dumping attacks in Windows environments
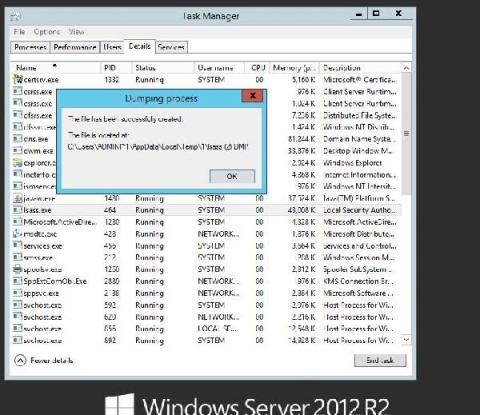
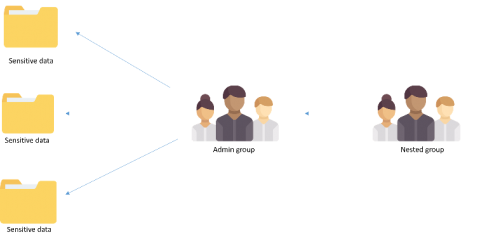
Most of the time, threat actors in the cybersecurity landscape don’t employ advanced techniques and tools to intrude and establish a foothold within networks. Often, they disguise malicious operations by mimicking the activities of legitimate users, leaving behind little to no footprint. Blending malicious actions with day-to-day IT activities helps attackers maintain a low profile and remain undetected for a longer period.