Operations | Monitoring | ITSM | DevOps | Cloud
Containers
The latest News and Information on Containers, Kubernetes, Docker and related technologies.
Kubernetes Observability Challenges: The Need for an AI-Driven Solution
Kubernetes provides abstraction and simplicity with a declarative model to program complex deployments. However, this abstraction and simplicity create complexity when debugging microservices in this abstract layer. The following four vectors make it challenging to troubleshoot microservices.
Leap-Frog Over your Kubernetes Obstacles
In this episode of Coffee & Containers, Bruno Andrade, Founder/CEO @ Shipa and Melissa McKay, Developer Advocate @ JFrog discuss some specific Kubernetes related obstacles.
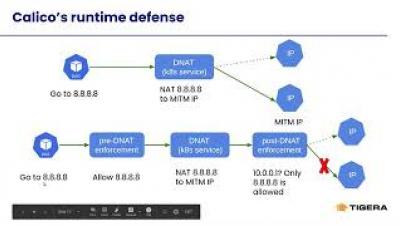
Calico Enterprise Multi Cluster Management - Federated Identity and Services
Lesson 2: Build generic Docker images
Coffee & Containers - "Leapfrog Over Your Kubernetes Obstacles"
Best Practices for Kubernetes Monitoring
Kubernetes, also known as K8s, is a container-orchestration platform for automating deployment, scaling, and operations of applications running inside the containers across clusters of hosts. Google open-sourced the Kubernetes project in 2014. According to a recent CNCF survey, Kubernetes is the most popular container management tool among large enterprises, used by 83% of respondents. Containers are a good way to bundle and run applications.
Assessing Reliability Risks on Kubernetes Clusters
Peter Grant, Kalai Wei, Gustavo Franco, Corey Innis, and Alexandra McCoy contributed to this post. The VMware Customer Reliability Engineering (CRE) team is proud to announce an open source Reliability Scanner for Kubernetes! It includes an extensible set of reliability assessments, or checks, performed against various components of a cluster, such as Pods, Namespaces, Services, etc. Operators can then configure appropriate constraints for the checks on their clusters.
Surviving the Disaster: How to Identify Bugs Immediately and Get Back on Track
As all developers know, when building software things don’t always go as planned. In fact, most of the time they don’t. With today’s modern distributed architectures it’s more important than ever to have the proper tools in your toolbelt. This allows us to automate as much of the software delivery lifecycle as possible and then be able to immediately triage issues when they arise.
What Is Zero Trust & How Do We Implement It to Run Secure CI/CD Workflows in Kubernetes?
Zero trust is a security concept that is centered around the idea that organizations should never trust anyone or anything that does not originate from their domains. Organizations seeking zero trust automatically assume that any external services it commissions have security breaches and may leak sensitive information.