Operations | Monitoring | ITSM | DevOps | Cloud
Elastic
Visualizing COVID-19 with Elastic
Logging in Spring Boot with the Elastic Stack
Let's look at the good parts of logging:
- How can you bring logging to production quickly?
- How does this work with Spring Boot in as a practical example?
- Do you want to add tracing and make the most of the combination?
- How do you manage the data that you are collecting?
GetSet Learning: Evolving with Elastic
Examining OpenData with a Search Index using Elasticsearch
Finding a home (and career) in the open source community
Open source software development can have a reputation for abrasive behavior. The search community is a clear counterexample for me, with a culture that emphasizes respect and acceptance. This culture played an important part in my own path to open source development. A little over six years ago, I was a wide-eyed software engineer settling into my first full-time job.
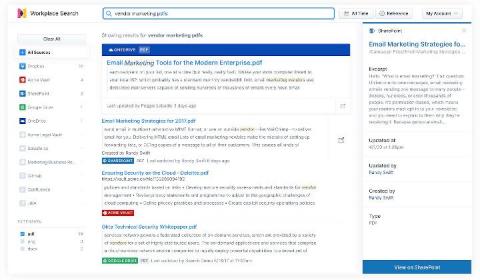
Searching Microsoft's cloud productivity suite with Elastic Workplace Search
If your organization is like virtually every other in the world (including ours!), you use a mix of Microsoft products in your productivity stack, possibly including SharePoint, Office 365 and OneDrive. But you probably also rely on a variety of other applications, maybe even mingling in “competing” tools like G Suite or Dropbox, in addition to complementary tools like Zendesk or GitHub.
Ingram Micro chooses Elastic to bolster search, sales on ecommerce site
Ingram Micro is a Fortune 100 company with $50 billion plus in revenue and operating in 56 countries. As the global leader in delivering technology and supply chain services to businesses, Ingram Micro touches about 80% of all high tech products sold around the world. Andre Dykhno, Head of Product for Global ecommerce, says ecommerce has been a large contributing factor to Ingram Micro’s modern day successes.
Adversary tradecraft 101: Hunting for persistence using Elastic Security (Part 2)
In Part 2 of this two-part series, our goal is to provide security practitioners with better visibility, knowledge, and capabilities relative to malicious persistence techniques that impact organizations around the world every day. In this post, we’ll explore two additional persistence techniques that are being used by attackers in the wild: Scheduled Tasks (T1053) and BITS Jobs (T1197).
The Elastic Stack: Free. Open. Limitless.
From the very beginning, the Elastic Stack — Elasticsearch, Kibana, Beats, and Logstash — has been free and open. Our approach is not only to make our technology stack available for free, but to make it open — housed in public repositories and developed through a transparent approach with direct involvement from the community. Two simple principles — free and open — broke down barriers and enabled many amazing things.