Github Checksums and Broken Pipelines: How to Prevent Disruptions
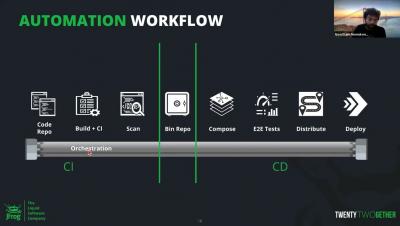
This week, GitHub changed how the archives they provided are made. The result of this change surprised developers, triggering pipeline failures all over the world in most ecosystems. This change has thankfully been retracted. Hear from JFrog Developer Advocate, Christopher McArthur on why this took place and the best practices to prevent future disruptions to your pipelines.