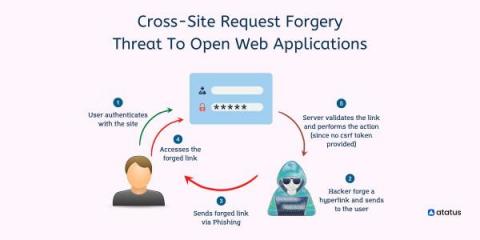
Cross-Site Request Forgery - Threat To Open Web Applications
Cross-site request forgery (CSRF) is an attack that tricks a user's browser into sending a malicious HTTP request to another website. This malicious HTTP request looks like it was sent by the user, but it actually comes from the attacker. A cross-site request forgery (CSRF) attempts to execute a change rather than trying to download personal data. Once an attack is executed there is no way for the attacker to directly monitor the result so attackers often execute multiple forgeries.