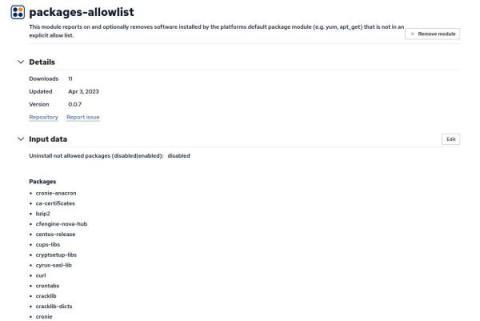
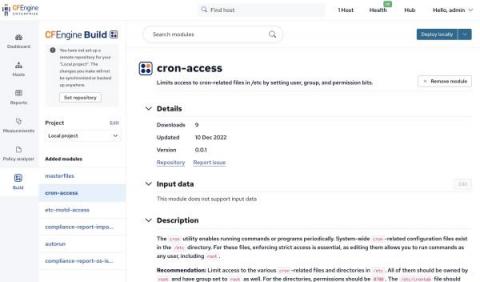
CFEngine 3.22 released - Coordination
Today, we are pleased to announce the release of CFEngine 3.22.0! The focus of this new version has been coordination. This is a non-LTS (non-supported) release, where we introduce new features for users to test and give feedback on, allowing us to polish before the next LTS.(CFEngine 3.24 LTS is scheduled to release summer 2024).