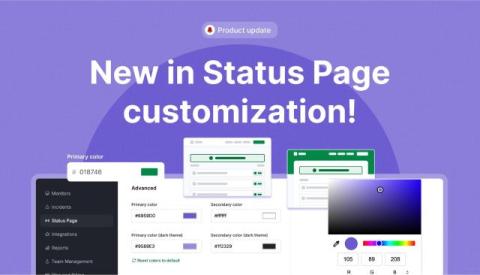
Improved subscriber management
We’re excited to introduce new features and improvements that make managing subscribers on your status page easier and more efficient. With these updates, you can invite subscribers, customize subscription settings, and keep everyone informed with just a few clicks. Here’s what’s new.