Operations | Monitoring | ITSM | DevOps | Cloud
ManageEngine
How to perform a skill-gap analysis
One of the first requirements of building an effective team that consistently delivers results is having dynamic team members with the right skill set. This means having the right number of people with the right skills working on your projects at the right time.
How to monitor IIS effectively
Microsoft Internet Information Services (IIS) is a popular web server for hosting web applications and is widely used in many sectors, such as healthcare, banking, e-commerce, logistics, etc. The IIS web server is the backbone of many IT infrastructures. But if the IIS web server encounters problems, it can lead to websites and applications experiencing higher response times, and timeouts resulting in end-users either leaving your website or complaining about the performance.
How to ensure network compliance in this era of remote work: The ITOM Podcast [Episode 5]
The ITOM Podcast returns with yet another episode to help you eliminate all the remote work woes in your IT environment. In the last episode, we discussed in detail about the key areas enterprises need to monitor to ensure endpoint security, measures to adopt to ensure cybersecurity while rolling out BYOD policies, and the crucial factors that IT leaders need to know about in the post-pandemic era with respect to IT security.
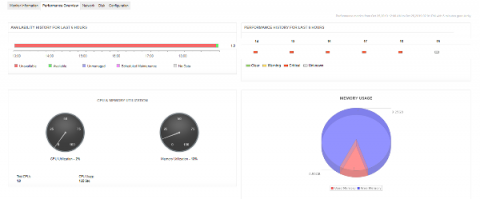
Transform the way you manage IT operations with the right network monitoring solution
Business-critical operations rely heavily on network performance. This means there’s a ton of pressure on IT teams to monitor the network effectively. There are numerous aspects to network monitoring, including virtual server monitoring, automation, baseline violation alerting, event logging, availability monitoring, and health monitoring.
How to defend your IT assets while implementing BYOD policies: The ITOM Podcast [Episode 4]
Gear up! The ITOM Podcast is back with an all new episode intended to help you surmount all your remote work challenges in an IT environment. In the last episode, we discussed VPN monitoring in detail, the challenges encountered while monitoring VPNs, and the key metrics to track to overcome those challenges. This week, we will deep dive into endpoint security and BYOD policies.
Best practices for your cloud monitoring strategy
With the advent of cloud technologies, there has been a major shift in the way organizations handle infrastructure operations and service delivery. The increasing shift towards cloud-based and hybrid cloud ecosystems for business operations has made it necessary for organizations to employ cloud monitoring tools that monitor the performance and efficiency of these cloud-hosted services.
4 ways to save on IT costs in the asset life cycle [Part 4: Retirement and disposal]
Welcome back to the final part of our four-part blog series on saving on IT costs in the asset life cycle. In the last part, we talked about how to cut costs during maintenance and support. In this part, we’ll look at retirement and disposal, and ways to save during this phase. The retirement phase of the asset life-cycle can be tricky, because asset managers have to accurately judge the time frame for when a certain asset is ready for retirement.
Hassle-free IP and switch port management with NetFlow Analyzer's IPAM SPM add-on
“The IP of that device? Let me look it up in this spreadsheet with a never-ending list of IP addresses! *sigh*” Sound familiar? Do you often need to block a certain port allowing unauthorized traffic, get the MAC address of the IP taking up most of your bandwidth, or scan for rogue devices entering your network? Then the IPAM SPM add-on is the solution for you!
Five worthy reads: Ethical AI: Why is it the need of the hour?
Five worthy reads is a regular column on five noteworthy items we have discovered while researching trending and timeless topics. This week, we highlight the urgent need for ethical AI due to increased adoption of AI enabled technologies by businesses during the COVID-19 pandemic.