Operations | Monitoring | ITSM | DevOps | Cloud
Kentik
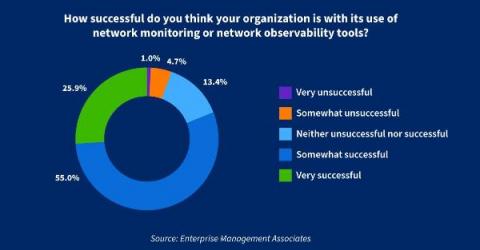
Are you a network observability champion?
At Kentik, we pride ourselves as innovators and thought-leaders for network observability. “Kentik is network observability” is more than a slogan for us. It’s an idea that informs our product roadmap and guides our problem-solving with customers. We’ve done a lot to explain network observability to prospects.
Kentik Market Intelligence just increased its IQ - introducing KMI Insights!
Early this year we launched Kentik Market Intelligence (KMI). If you missed it, KMI enumerates transit and peering relationships as well as produces rankings based on the volume of IP space transited by ASes in different geographies. Using tables and charts, KMI offers a global view of the internet out-of-the-box without any configuration or setup. KMI uses public BGP routing data to rank ASes based on their advertised IP space.
Insight and reliability through continuous synthetic testing in Kubernetes
Kubernetes has become the de facto standard for cloud-based applications. As companies migrate more and more workloads, ensuring reliable connectivity and performance are critical not just for user applications but also for the cluster itself. In this article, we will discuss how augmenting your system monitoring with in-cluster synthetic testing can give you proactive indicators that something might be headed for trouble.
Managing the hidden costs of cloud networking - Part 2
In the first post of this series, I detailed ways companies considering cloud adoption can achieve quick wins in performance and cost savings. While these benefits of the cloud certainly remain true in theory, realizing these benefits in practice can be increasingly difficult as applications and their networks become more complex.
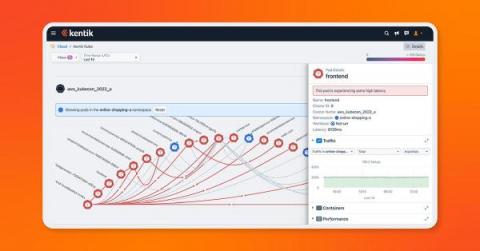
Kentik Kube extends network observability to Kubernetes deployments
We’re excited to announce our beta launch of Kentik Kube, an industry-first solution that reveals how K8s traffic routes through an organization’s data center, cloud, and the internet. With this launch, Kentik can observe the entire network — on prem, in the cloud, on physical hardware or virtual machines, and anywhere in between.
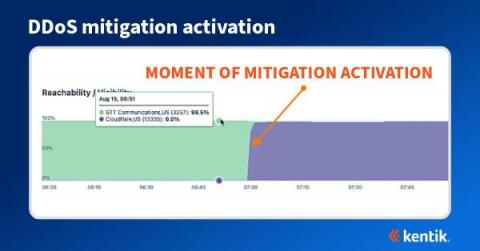
How BGP propagation affects DDoS mitigation
We often think of DDoS attacks as volumetric malicious traffic targeted against organizations that effectively take a service offline. Most frequently detected by anomalous behavior found in NetFlow, sFlow, IPFIX, and BGP data, what may not be well understood is how the DDoS mitigation works and how it’s possible to visualize the effectiveness of the mitigation during and after an attack.
How BGP propagation affects DDoS mitigation
Detecting and Mitigating DDoS Attacks
Flows vs. packet captures for network visibility
Recently, I saw some discussion online about how flow data, like NetFlow and sFlow, doesn’t provide enough network visibility compared to doing full packet captures. The idea was that unless you’re doing full packet captures, you’re not doing visibility right. Because I’ve used packet captures so many times in my career, I admit there’s a part of me that wants to agree with this.