Anatomy of an OTT traffic surge: Thursday Night Football on Amazon Prime Video
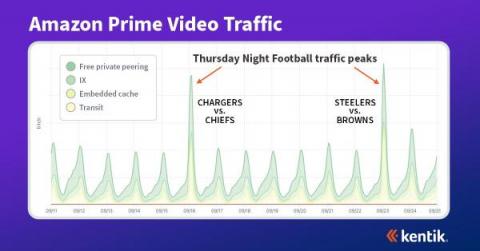
This fall Amazon Prime Video became the exclusive broadcaster of the NFL’s Thursday Night Football. This move continued Prime Video’s push into the lucrative world of live sports broadcasting. While they had previously aired TNF, as it is known, this is the first season Amazon Prime Video has exclusive rights to broadcast these games. As you can imagine, airing these games has led to a surge in traffic for this OTT service.