Best Practices for Database Performance Monitoring
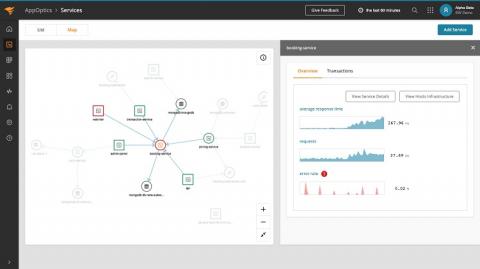
Like application monitoring, database performance monitoring is a critical discipline. If there isn’t a code issue, there’s a good chance you have a database issue. Key metrics such as CPU and memory usage can give you important insights into your database’s performance. In addition, by monitoring slow queries, and inordinate number of database requests, you can combine this knowledge to optimize both.