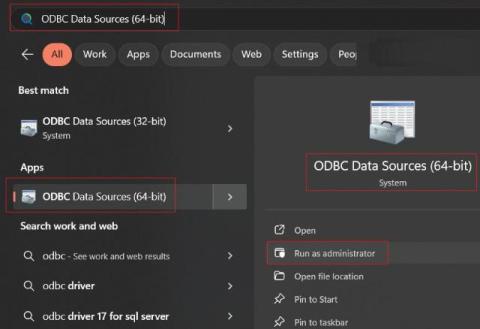
What Are Network Monitoring Agents & How to Deploy & Configure Them
In this article, we’ll dive into the video where we discuss Network Monitoring Agents in Obkio’s Network Performance Monitoring App. Monitoring Agents (software, hardware, virtual appliances) are deployed in key network locations to monitor performance between all network sites. This video will also teach you how to create new Monitoring Agents or to modify or delete Agents you already have in your account. .