Continuous Intelligence for Atlassian tools and the DevSecOps Lifecycle (Part 2)
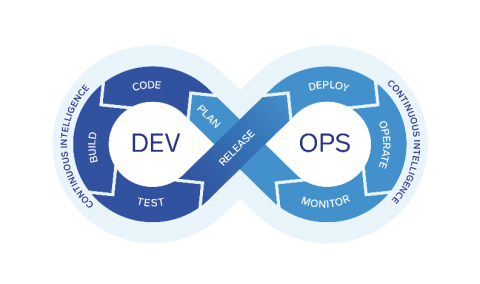
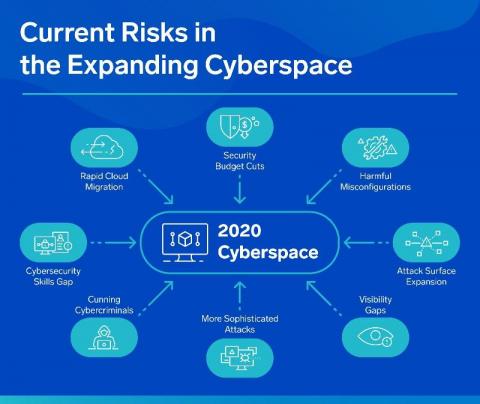
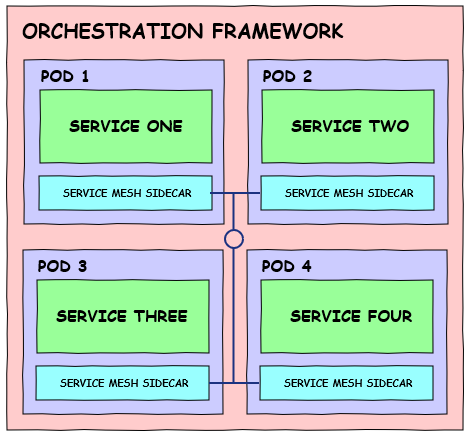
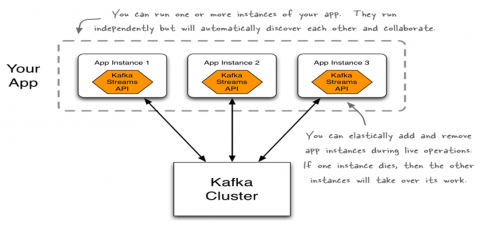
Today’s modern deployment pipeline is arguably one of the most important aspects of an organization’s infrastructure. The ability to take source code and turn it into a production application that’s scalable, reliable and highly available has become an enormous undertaking due to the pervasiveness of modern application architectures, multi- or hybrid-cloud deployment strategies, container orchestration and the leftward movement of security into the pipeline.