How to Read, Search, and Analyze AWS CloudTrail Logs
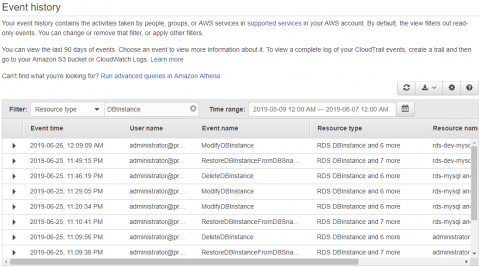
In a recent post, we talked about AWS CloudTrail and saw how CloudTrail can capture histories of every API call made to any resource or service in an AWS account. These event logs can be invaluable for auditing, compliance, and governance. We also saw where CloudTrail logs are saved and how they are structured. Enabling a CloudTrail in your AWS account is only half the task.