Operations | Monitoring | ITSM | DevOps | Cloud
April 2022
Microsoft will disable SMB1 client this year, what does this mean for your customers?
To be clear, SMB V1 has been deprecated, unsecure, and not recommended for a long time. But Microsoft is now taking the next step towards removing it from Windows entirely. In recent years, Microsoft had stopped installing SMB1 server on all Windows versions by default; however, they have kept installing the SMB1 client in Home and Pro versions of Windows. This was meant to allow end users to connect to various devices, including NAS, which only supported SMB1.
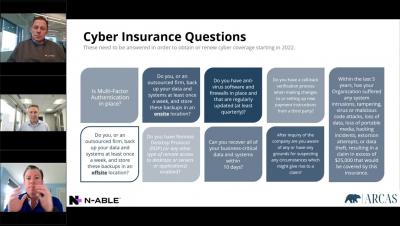
The Anatomy of a Cybercrime: Dissecting a Phishing Attack
Our previous blog provided an outline of the current phishing trends and potential consequences of not being aware of them. This article, however, takes a deep dive into a particularly dangerous type of attack. There is a large amount of phishing that is targeting webmail users on non-free mail domains in an attempt to syphon out their credentials for later use.
Windows Autopatch: Will MSPs Still Need a Patch Management Solution?
On April 5, 2022, Microsoft announced their new Windows Autopatch feature to take the burden of patching off the shoulders of overwhelmed IT departments. With a planned released date of July 2022, it’s worth getting educated about this new service from Microsoft and what its potential impacts on the MSP ecosystem will be. Spoiler alert: It’s not that big of a deal.
10 Tips to Creating a Website That Will Improve Prospect Conversion and Engagement, Part Two
Did you know? 75% of users admit to making judgments about a company’s credibility based purely on how their website looks and functions. So, it’s imperative that the design of your website doesn’t deter people from clicking through your site and heading straight to your competition. Continuing from my previous blog, looking at 10 things you can do to ensure your website is as engaging as it can be. Here are tips six to ten.
2022 MITRE ATT&CK Evaluation Results Are In-What You Need to Know
It’s that time of the year again! The MITRE Engenuity ATT&CK evaluation results are in and generating quite the buzz in the industry. And for good reason. The MITRE Engenuity ATT&CK evaluation focuses on a tool’s ability to prevent and detect cyber attacker behaviors. Now in its fourth round of testing, it has become the de-facto standard for how security solutions perform against different advanced cyberattack scenarios.
Monitoring Hyper-V and ESXi-what should you do?
Over the years, I found that building out monitoring scripts and using them properly has proven to be a challenge. When I look back at my internal IT days using platforms like Whatsupgold, PRTG, or N-central, the question always remained the same: how can I monitor efficiently and get alerts that matter? In this blog post, I thought I’d tackle something that is a challenge for a lot of people: monitoring Hypervisors.
Be Proactive Amid Growing Cyber Security Concerns
Over the past few weeks, we’ve all been paying very close attention to the events unfolding in eastern Europe. As an individual, it’s heartbreaking to see a war break out and the impact it’s having across the region. We know that cyberattacks are now a part of war. We also know cyberattacks can be targeted, but also have the potential for unintended consequences and increased impact as they can spread outside of the initial target.
Getting Smart with M&A, Part One-Why Standardization Is Critical
In my previous blog, I looked at what’s currently going on in the MSP market with respect to mergers and acquisitions. I also set the scene to discuss some of the key things we’ve learned from this activity and how this is helping to shape the way we are supporting our partners that are going through this process.
Double Click to Install: Create a PKG even your users can install from
You’ve got a script. Maybe you wrote it or maybe you found it online, but it handily solves a problem your users face or does a task you typically spend several minutes on with a single command many times a day. With any RMM platform, it would normally be a simple matter of deploying the script to those devices, setting the schedule for it to run, then sitting back and sipping your beverage of choice. Unless you’re in the server room—no food or drink in the server room.