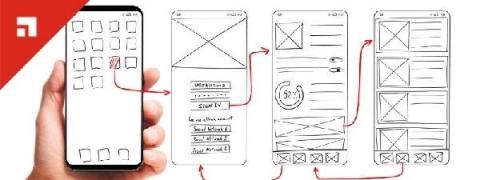
Applying Strong Cyber Hygiene Security to IoT Endpoints
The Internet of Things, better known as IoT. You’ve heard of it, right? But do you know what it is? Simply, it is the interconnection of things (or endpoints) on the Internet to send and receive data. Today, experts calculate that there are 31 billion things connected to the insecure Internet, and growing exponentially. Did you know there are different types of IoT applications?