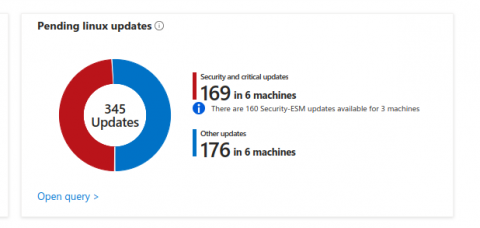
Reducing latency in industrial systems with real-time Ubuntu on Intel SoCs
Delivering a comprehensive real-time solution for industrial systems requires careful work at every layer of the stack. Since standalone hardware or software components are not sufficient, Canonical and Intel have joined forces to deliver an out-of-the-box real-time solution. This solution is now generally available on Intel Core processors.